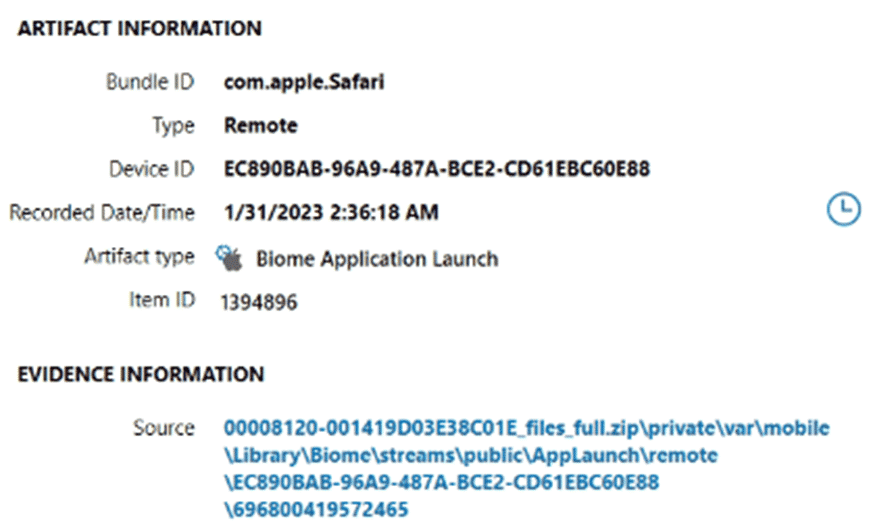
Apple's Biome: The Successor to knowledgeC on iOS
A deep dive into Apple's Biome (SEGB) database, its relationship to knowledgeC, and the implications for digital forensics.
Apple’s iOS devices are a treasure trove of user data, much of which is valuable in digital forensics investigations. For years, the knowledgeC.db database was a crucial source of information, providing insights into user activity, application usage, and device interactions. However, with recent iOS versions, Apple has transitioned to a new system known as “Biome,” identified by the file signature “SEGB”. This shift has significant implications for digital forensics practitioners.
A Brief History of knowledgeC
The knowledgeC.db database, often referred to simply as “knowledgeC,” is a SQLite database that first appeared around iOS 8. It’s designed to store a wealth of information about user and device interactions, leveraging CoreDuet technology. This data includes:
- Application Usage: Which apps were used, when, and for how long.
- Device State: Information on device lock/unlock events, charging status, and battery levels.
- Location Data: Inferred location information, even when precise GPS data isn’t available.
- Intent History: Data related to Siri suggestions and app interactions.
- Safari History: Browsing Activity
- Bluetooth and Wifi Connections
This database became a cornerstone of iOS forensics, providing a timeline of user activity that could be crucial in investigations. Tools like iLEAPP and others were developed to parse and interpret the complex data structures within knowledgeC.
Enter Biome (SEGB)
Starting with more recent iOS versions (iOS 15 and later, this transition has been ongoing), Apple began phasing out knowledgeC in favor of a new system called Biome. The files associated with Biome are characterized by the “SEGB” file signature at the beginning of the file. This gave rise to the informal name “SEGB files” within the digital forensics community.
1
2
#Example Hexdump
00000000 53 45 47 42 04 00 00 00 00 00 00 00 00 00 00 00 |SEGB............|
The origins of the “SEGB” designation are, indeed, somewhat humorous. The name arose because “SEGB” is simply the file header found in these files. The DFIR community adopted it as a convenient shorthand, as Apple hadn’t (and still hasn’t) publicly documented the format extensively. it looks like the name stuck, and its refered to both as Biome and SEGB.
Biome aims to achieve similar goals to knowledgeC – tracking user and device activity – but it uses a different underlying architecture. Instead of a single SQLite database, Biome is distributed across multiple files, each containing specific types of data. These files are often found within directories related to specific apps or system services.
Key Differences and Challenges
The shift from knowledgeC to Biome presents several key differences and challenges for forensic examiners:
- Data Distribution: Unlike the centralized
knowledgeC.db, Biome data is spread across numerous files, making it more challenging to locate and correlate information. The directory structures and naming conventions can vary, requiring careful examination of the file system. - File Format: SEGB files are not SQLite databases. They use a proprietary Apple format, which is not publicly documented. This means that existing SQLite-based parsing tools are not directly applicable.
- Data Interpretation: Even with access to the raw data, understanding the meaning and context of Biome entries can be challenging. The relationships between different data points are often not immediately obvious.
- Evolution: Biome is still undergoing development, and its internal structure can change with new iOS updates. This makes it difficult to create tools for parsing.
- Encryption: Encrypted
Implications for Digital Forensics
The transition to Biome necessitates a shift in forensic methodologies:
- New Tools and Techniques: Examiners need new tools and techniques to parse and interpret SEGB files. The community is actively developing solutions, but progress is ongoing.
- File System Analysis: Thorough file system analysis is more crucial than ever. Understanding the directory structure and identifying relevant SEGB files is a key skill.
- Reverse Engineering: Some degree of reverse engineering may be required to fully understand the structure and contents of SEGB files. This is a complex and time-consuming process.
- Data Correlation: Connecting the dots between different Biome data points will be essential for reconstructing user activity. This requires a deep understanding of how iOS uses Biome.
Example: Locating Biome Files (Bash)
While a complete parsing solution is still under development, here’s a simple Bash command to help locate potential Biome files on an iOS file system dump:
1
find /path/to/filesystem -type f -print0 | xargs -0 file | grep "SEGB"
This command searches for files (-type f) within the specified file system path, pipes the output to xargs to handle filenames with spaces, and then uses file to identify files containing the “SEGB” signature.
Example: Locating Biome Files (PowerShell)
and, the powershell way:
1
2
3
4
5
Get-ChildItem -Path "C:\path\to\filesystem" -File -Recurse | ForEach-Object {
if ((Get-Content $_.FullName -Encoding Byte -First 4 | ForEach-Object { [char]$_ }) -join '' -eq 'SEGB') {
Write-Host "Found SEGB file: $($_.FullName)"
}
}
This powershell script gets all files recursively in the root directory, reads the first four bytes of each, convert those bytes to characters, and checks if the result is ‘SEGB’.
Conclusion
Apple’s Biome represents a significant evolution in how iOS tracks user activity. While it presents challenges for digital forensics, it also offers the potential for even more granular insights into device usage. As the forensic community continues to research and develop tools for analyzing Biome data, it will undoubtedly become another valuable source of evidence in investigations. The transition highlights the ongoing need for adaptability and continuous learning in the field of digital forensics.